In 2025, 72% of organizations reported rising cyber-risks, and 35% of small enterprises acknowledged insufficient cyber resilience, marking a sevenfold increase since 2022. These findings underscore a growing gap between threat exposure and organizational preparedness. Rather than focusing solely on preventing breaches, experts now emphasize minimizing the impact of cyber incidents as a more realistic and strategic objective. n nCyber resilience refers to an organization’s capacity to maintain core operations and achieve objectives during and after a major digital attack. To determine whether an entity is truly resilient, measurable indicators are essential. Without systematic assessment, vulnerabilities may remain undetected until exploited, leading to reactive responses that drain resources and hinder long-term security improvements. n nEffective measurement moves beyond vague descriptions and enables data-driven decisions. It supports leadership in allocating budgets, gives regulators verifiable proof of compliance, strengthens customer confidence, and aligns teams around high-impact improvements. When embedded into regular operations—similar to financial audits—resilience metrics become a strategic language connecting governance, risk management, and daily practices. n nCurrently, no single framework fully captures all aspects of cyber resilience. Instead, organizations rely on a mix of partial tools: ISO 27001 and CIS Controls assess foundational cyber hygiene; CBEST and MITRE’s ATT&CK Evaluations test detection and response through simulated attacks; Basel principles enhance recovery planning; and FAIR helps quantify risk levels. n nTo build a comprehensive view, measurement should integrate technical systems, human behavior, and organizational processes. Key principles include simplicity to encourage adoption, holistic design to reflect cross-functional dependencies, use of adaptive indicators instead of rigid metrics, and flexibility to accommodate diverse goals and audiences. Assessments should prioritize actionable insights that guide interventions and track progress over time. n nThe World Economic Forum’s Cyber Resilience in Industries initiative brings together stakeholders from industry, government, and academia to develop unified measurement approaches. By identifying gaps in existing models and promoting collaboration, the initiative aims to drive consistent, measurable enhancements across sectors. n nAs digital interdependence grows and threats evolve, the cost of inadequate resilience assessment rises. Organizations that treat cybersecurity as an enterprise-wide responsibility—not just an IT function—and embed measurement into routine operations can shift from crisis response to proactive risk management. This integration ensures resilience becomes part of the organizational culture, not merely a fallback during system failures. n— news from The World Economic Forumn
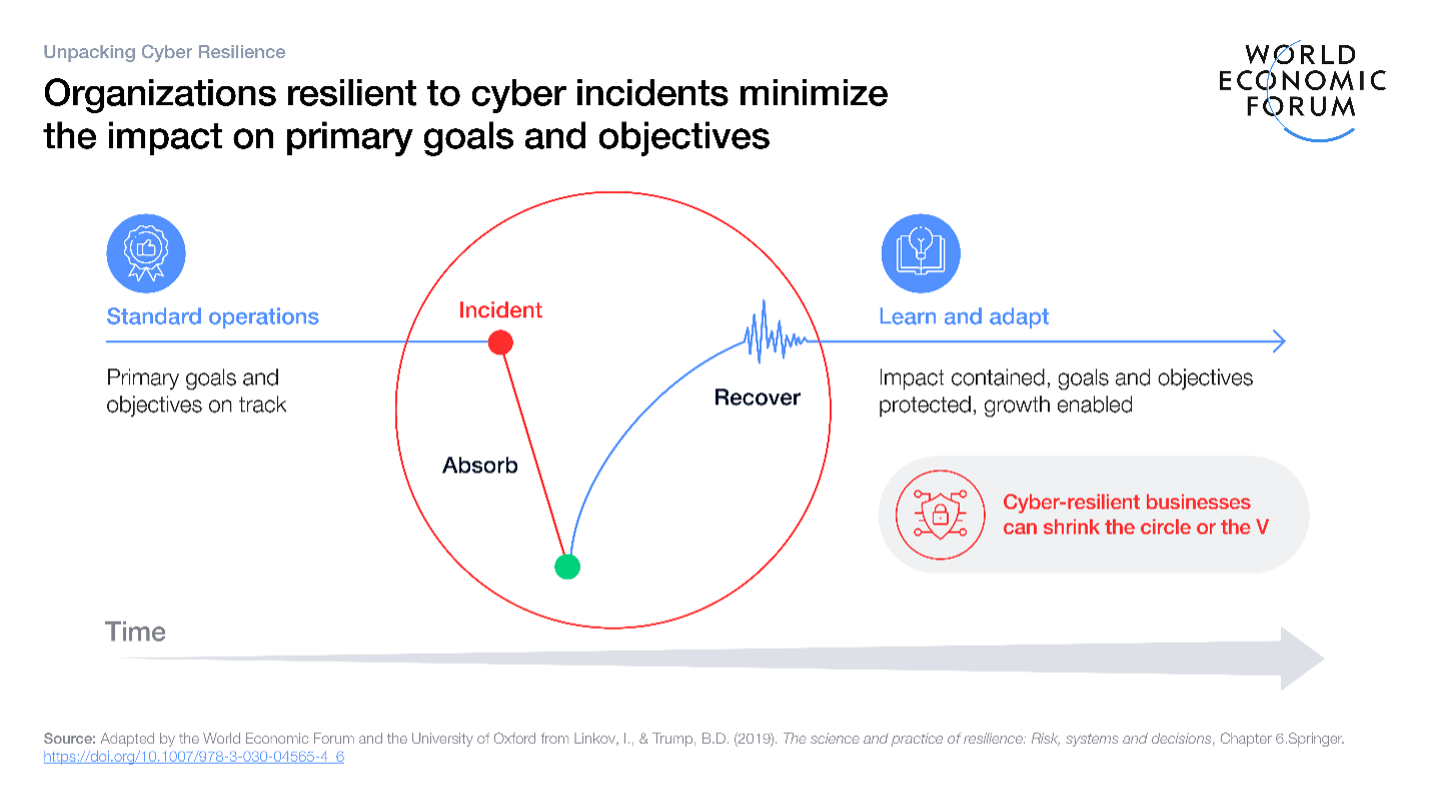
— News Original —nCyber resilience: Moving beyond prevention to boost securityn72% of organizations report an increase in cyber-risks and one in three small businesses say their cyber resilience is insufficient. n nOrganizations must embed cyber resilience across their entire body, rather than leaving it as an IT-only issue. n nTo be effective, cyber resilience needs to be measured with meaningful data. n nIn 2025, 72% of organizations reported an increase in cyber-risks and 35% of small businesses said their cyber resilience was insufficient. This represents a sevenfold increase since 2022. n nCompanies can’t prevent every cyber incident and so being able to minimize the impact is just as, or even more, important as preventing incidents from happening in the first place. The focus shouldn’t be: “How do we stop every attack?”, but rather: “How do we survive any attack?” n nThis is cyber resilience in practice: an organization’s ability to minimize the impact of a significant cyber incident on its primary goals and objectives. n nSo, if resilience is about outcomes, how can an organization know if it’s truly resilient? How can leaders prove resilience to boards, insurers, regulators, employees – and to themselves? n nFailure to understand an organization’s cyber resilience posture can leave it exposed. And without measurement, weaknesses can remain hidden until a major incident exposes them. Taking a reactive, rather than proactive, approach creates a vicious cycle that drains resources, making less effort available for the very thing that would prevent more incidents. n nBy measuring cyber resilience, however, an organization can better protect itself and its wider ecosystem from the effects of cyberattacks. n nHow to measure cyber resilience n nMeasurement helps to describe the world beyond vague terms such as “long”, “heavy” or “soon”. While it’s not possible to quantify everything, businesses can rely on data for anything that can be measured, which allows them to understand the status quo and prioritize actions that will enable agility. n nThe true value of measurement lies in how it informs people and choices. It gives executives clarity for investment decision making, provides regulators with credible evidence of resilience, builds customer trust in products and services, and helps teams to focus on the most impactful improvements to any processes they are measuring. Data underpins better decision making and provides a foundation for multiple stakeholders to build a shared understanding of the resilience of the organization ‘s ecosystem. This is how measurement becomes the language that connects strategy, compliance, customer confidence and day-to-day practice. n nTo date, no single comprehensive framework exists to measure cyber resilience holistically. Instead, the current landscape consists of multiple overlapping but partial approaches – such as cyber maturity models, threat-led testing frameworks and operational resilience frameworks – each covering specific dimensions of the cyber-resilience challenge. n nCybersecurity frameworks like ISO 27001 and CIS Controls focus on assessing cyber hygiene and maturity, for example. Threat-led testing schemes such as CBEST and frameworks or methodologies like STAR-FS and MITRE ‘s ATT&CK Evaluations emphasize adversarial simulation and detection capabilities. Meanwhile, frameworks like the Basel principles boost resilience and recovery and planning, while FAIR helps quantify and prioritze cyber-risk . n nMeasuring cyber resilience requires moving beyond static assessments and security-focused benchmarks. It should integrate technical, human and organizational factors, while remaining adaptive to evolving threats and contexts. n nKey principles for measuring cyber resilience include: n nKeep tools simple to support adoption, allow repeat assessments and encourage broad organizational engagement. n nUse a holistic approach by combining technical readiness with human and organizational factors to account for the cross-organizational nature of cyber resilience. n nConsider cross-organizational factors to avoid a narrow focus on security. n nChoose indicators or indices over fixed metrics to reflect evolving baselines, prevent too much focus on a single area and avoid unhelpful comparisons. n nIntegrate flexibility to accommodate different definitions of resilience, varying goals and changing audiences across organizations. n nPrioritize decision making through assessments that allow organizations to make interventions, guide decisions and track progress. n nCreate measures and results that support leadership’s strategic decision making and enable cultural change. n nTaking action on cyber resilience n nThe World Economic Forum’s Cyber Resilience in Industries initiative unites perspectives from industry, government, academia and civil society to build a shared approach to measuring cyber resilience. The initiative draws on lessons from existing frameworks, identifying critical gaps and developing actionable cybersecurity insights for leaders. By fostering collaboration across sectors, the initiative aims to advance consistent, measurable improvements in organizational and systemic cyber resilience. n nAs digital ecosystems grow, interconnections deepen and threat actors become more sophisticated, the cost of unmeasured cyber resilience will continue to rise. Waiting for a breach to reveal weaknesses could cost a company millions of dollars or even drive it out of business. n nTo avoid this, core business functions must become cyber-resilient, it should not just be seen as an IT concern. Embedding measurement into operational cyber routines – just like it’s embedded in financial audits or risk assessments – will enable the necessary shift from reactive crisis management to proactive risk mitigation. This is how cyber resilience becomes part of an organization’s DNA, not just a last resort when systems fail.